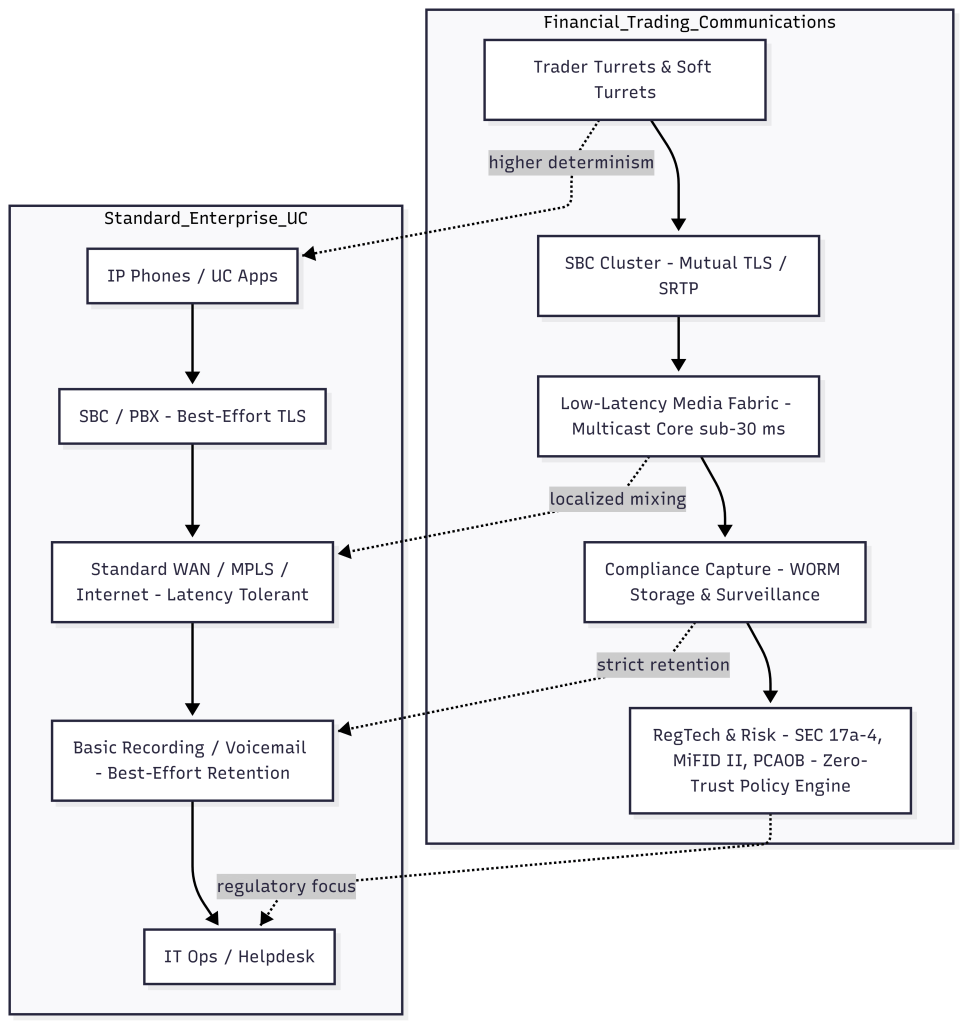
- Financial vs. Typical Enterprise Communications
- Threat Model and Zero-Trust Guardrails
- Turret Phones for Trading Floors
- DevSecOps applied top the entire assembly of microservices and integrator
- Secure Voice and Collaboration Stack
- Application Security and DevSecOps Fabric
- Monitoring, Analytics, and AI-Augmented Response
- Compliance, Governance, and Benchmark Alignment
- Threat Intelligence and Risk Modeling
- References
I build one of the popular soft-turret stacks that bolts WebRTC agility onto legacy hardware turrets, and the elevator pitch always sounds easier than the engineering reality. Traders expect the tactile “instant connect” of their button-packed boards, but we’re stitching together globally distributed media planes, compliance capture engines, and metrics in clouds that never sit still. Matching the speed and feel of copper-based systems means chasing sub-30 ms round trips, taming jitter on home broadband, and squeezing every millisecond out of TLS handshakes—all while preserving five-nines uptime and SEC-grade audit trails. This doc captures the blueprint (and battle scars) from turning that hybrid dream into something traders can slam with confidence.
Financial vs. Typical Enterprise Communications
The financial stack layers deterministic low-latency media routing, integrated compliance capture, and prescriptive retention controls above the core UC services, while mainstream enterprise deployments focus on collaboration breadth and best-effort security with lighter regulatory obligations.
Threat Model and Zero-Trust Guardrails
Trading floors are neon-lit treasure troves for market manipulation, CDR theft, and ransomware crews. Zero trust turns the lights on everywhere: continuous verification, least privilege, and granular segmentation keep lateral movement in check even if an endpoint gets burned. NIST SP 800-207 lays out how to plant policy decision points across SIP trunks, SBCs, and API gateways [5], while the NIST CSF families (Identify, Protect, Detect, Respond, Recover) turn those controls into scorecards executives can actually read [6].
There are a number of measures that can be taken to provide security to calls against malicious users:
- Secure communication protocols: It is important to use secure communication protocols, such as SIP over TLS (Transport Layer Security) or SRTP (Secure Real-time Transport Protocol), to encrypt calls and protect them against interception and tampering.
- Authenticate users: Implementing authentication mechanisms, such as passwords or two-factor authentication, can help to prevent unauthorized users from accessing the phone system.
- Monitor for unusual activity: Regularly monitoring the phone system for unusual activity, such as unexpected calls or patterns of usage, can help to identify and prevent potential threats.
- Implement firewall and intrusion prevention systems: Firewall and intrusion prevention systems can help to protect the phone system against external threats, such as malware or hackers.
- Security software: Installing security software, such as antivirus or anti-malware software, can help to protect against threats that may be transmitted over the phone system.
Financial telecommunication is a subset of telecom systems that cater to the need for highly secure and customized call plans used in the financial sector. Some examples of this can be soft turret phones which are used for trading stocks.
Turret Phones for Trading Floors
Trading platform supports voice, video, IM, e-mail and other multimedia communications services across a range of devices and communications standards to meet the exacting requirements that financial industry for secure and super-fast communication. Financial institutions rely on turret phones and multi-channel trader voice platforms to exchange high-value orders, capture voice recordings for audit, and coordinate with global liquidity venues. Regulations such as SEC Rule 17a-4 mandate the preservation of voice and electronic communications, so the underlying cloud telephony stack must guarantee integrity, retention, and non-repudiation for every leg of a call path [4].

A hard turret phone based traditional trading platform is a TDM based switching solution. This has a limitation on standard interfacing, scalability and availability.SIP trading platforms for standard interfaces and solution is answer to these demands. A SIP trading platforms provide standard interfaces and solutions with add-ons like
- compatibility with existing turret consoles
- high transactions per second
- reliable multicast-enabled network
- artificially induced clarity and background noise reduction, Echo cancellation, packet loss concealment.
- Channel mixing
- Recording with PIP hiding such as address or credit card numbers
- Intelligent muting/ducking
- AAA security – Active Directory authentication
- preferred SLA of 5 9’s
- WebRTC-based soft client to make audio and video calls from/to soft and hard turret.
Keep the latency low is a critical requirement for such a communication solution and thus these should be localizing conferencing as much as possible to reduce the impact on WAN.
But modern turret ecosystems extend beyond TDM dealer boards to include SIP, WebRTC, and soft-client endpoints that can roam between data centers and controlled remote offices. A resilient implementation typically offers:
- Compatibility with legacy turret consoles while onboarding SIP/WebRTC clients for hybrid deployments.
- High transactions per second (TPS) signaling planes, reliable multicast-enabled audio distribution, and localized conferencing to minimize WAN latency for bursty quoting windows.
- Audio enhancements—echo cancellation, packet-loss concealment, adaptive noise suppression—and channel mixing for collaboration pods.
- Policy-driven recording that can mask payment card or client identifiers (PII/PCI redaction) while meeting retention rules.
- Intelligent muting/ducking, AAA backed by Active Directory, a WebRTC soft client for continuity, and a preferred SLA of 99.999% availability across metro-active/standby regions.
Software-first turret offerings from providers such as IPC Systems (Unigy), Cloud9 Technologies, and Speakerbus iTurret demonstrate how dealer boards are evolving into distributed trading collaboration suites with built-in compliance capture [17][18][19].
Application Security Infrastructure is a critical component to safeguard such solutions against malicious users or a possible attack on secure communication links or systems.
DevSecOps applied top the entire assembly of microservices and integrator
Like any communication service provider, a financial comm solution also has many parts such as CRM integrations , OSS, Enterprise policies, tracking and logging so on. Some of which are shown below. Secure the CICD pipeline and restrict access using roles and keys is an important step in development and rolling out new features.
Secure Voice and Collaboration Stack
- Protocol hardening: Start every session with SIP over TLS 1.3 and drop media into SRTP (or DTLS-SRTP when WebRTC joins the party) so metadata and waveforms stay encrypted in transit [1][2][3]. Mutual TLS between SBCs, soft-switch clusters, and upstream carriers keeps the peering circle tight.
- Authentication and authorization: Tie trader identities to hardware-bound certificates or phishing-resistant credentials, then let role-based policies govern who can pick up a shout line, launch a hoot, or blast a team channel.
- Network protections: Put dual firewalls and DDoS scrubbers ahead of the SBCs, segment east-west traffic into micro-VNets, and use brokered direct-connect or premium ISP circuits for deterministic QoS.
- Resilient conferencing: Keep mix/minus resources local to the metro so traders enjoy sub-30 ms experiences instead of hair-pinned WAN detours.
Application Security and DevSecOps Fabric
Today’s telephony control plane is a squad of microservices—call control, CRM adapters, compliance recorders, analytics engines—so defending the pipeline is just as important as guarding the media stream. NIST SP 800-204A backs a DevSecOps workflow with signed artifacts, scoped secrets, and admission controllers no matter if you deploy to Kubernetes, PaaS, or bare metal [7]. Core moves:
- Layer edge WAFs, internal service firewalls, and RASP to squash injection or deserialization attacks before they can hijack SIP logic.
- Monitor for behaviors that “feel wrong” for a dealer room (e.g., a hoot channel logging in from a faraway ASN) and trigger adaptive controls when they pop.
- Shield the riskiest APIs—order session sync, recording export— with tighter throttles and inspection rather than blanket network ACLs.
- Harden container images, protect endpoints on jump hosts, and verify supply-chain integrity for every voice algorithm you import.
- Use controlled direct-connect or ISP circuits for B2B peering and let SIP/FIX-aware IPS gear patrol those lanes.
Monitoring, Analytics, and AI-Augmented Response
Think of SIEM as mission control for trader voice. It blends SIM and SEM so coordinated fraud attempts are spotted before they mess with the market. Pipe in call detail records, SBC logs, and infra telemetry, then let AI helpers prioritize real incidents. Map detections to MITRE ATT&CK tactics, CAPEC patterns, and voice-centric scenarios like rogue auto-dialers or deepfake voice injection to keep runbooks sharp [13][14]. Automated response can bench suspicious extensions, flip signaling credentials, or trigger privacy-preserving review flows without scrambling humans at 2 a.m.
Compliance, Governance, and Benchmark Alignment
- PCI DSS 4.0: Required when handling payment card data over voice or IVR; tokenize sensitive digits before storage and enforce strict network segmentation [8].
- COBIT: Governs process ownership, risk metrics, and control objectives so technology, risk, and compliance teams stay aligned on voice transformation milestones [9].
- CSA Cloud Controls Matrix (CCM): Maps cloud telephony components (SBC-as-a-service, call transcription ML models) to unified cloud security controls [10].
- CIS Benchmarks and DISA STIGs: Provide hardening baselines for operating systems, databases, and session controllers that host trader voice workloads [11][12].
Threat Intelligence and Risk Modeling
- MITRE ATT&CK / CAPEC alignment: Catalog adversary behaviors (credential access, lateral movement) to inform purple-team exercises and compensate for any detection blind spots [13][14].
- STRIDE: Classify telephony risks—spoofing (caller-ID or SIP identity), tampering (CDR manipulation), repudiation (voice recording disputes), information disclosure, denial of service, and privilege escalation—to prioritize mitigation [15].
- DREAD scoring: Quantify risk by damage, reproducibility, exploitability, affected users, and discoverability, ensuring objective severity rankings for backlog triage [16].
Make the journey to build a secure financial communication platform feel like a relay, not a slog. Assess by inventorying turrets, SBCs, media gateways, clouds, and SaaS hooks, then map every data flow against SEC/PCAOB retention rules to reveal quick wins. Harden next: enforce SIP over TLS 1.3/SRTP, rotate certs, segment aggressively, and drop in voice-savvy IPS/WAF stacks so the signaling spine can take a punch. Automate the guardrails inside CI/CD with security scans and policy-as-code, and block releases that don’t meet container or infra baselines. Validate with frequent red/blue exercises inspired by MITRE ATT&CK and STRIDE storylines to prove recording redaction and lawful-intercept features work when stress-tested. Finally, Operate with centralized observability (SIEM + UEBA), AI-assisted playbooks, and quarterly health checks mapped to NIST CSF dashboards to keep momentum high.
References
- [1] IETF RFC 3261: SIP: Session Initiation Protocol — https://www.rfc-editor.org/rfc/rfc3261
- [2] IETF RFC 3711: The Secure Real-time Transport Protocol (SRTP) — https://www.rfc-editor.org/rfc/rfc3711
- [3] IETF RFC 8446: The Transport Layer Security (TLS) Protocol Version 1.3 — https://www.rfc-editor.org/rfc/rfc8446
- [4] U.S. Securities and Exchange Commission, Rule 17a-4 — https://www.sec.gov/rules/final/34-44992.htm
- [4a] SEC Rule 17a-4 Overview — https://www.sec.gov/rules/final/34-44992.htm
- [5] NIST SP 800-207: Zero Trust Architecture — https://csrc.nist.gov/publications/detail/sp/800-207/final
- [6] NIST Cybersecurity Framework — https://www.nist.gov/cyberframework
- [7] NIST SP 800-204A: Building Secure Microservices-based Applications — https://csrc.nist.gov/publications/detail/sp/800-204a/final
- [8] PCI Security Standards Council, PCI DSS v4.0 — https://www.pcisecuritystandards.org/document_library
- [9] ISACA, COBIT Governance Framework — https://www.isaca.org/resources/cobit
- [10] Cloud Security Alliance, Cloud Controls Matrix — https://cloudsecurityalliance.org/artifacts/cloud-controls-matrix
- [11] Center for Internet Security, CIS Benchmarks — https://www.cisecurity.org/cis-benchmarks
- [12] DISA Security Technical Implementation Guides — https://public.cyber.mil/stigs
- [13] MITRE ATT&CK — https://attack.mitre.org/
- [14] MITRE CAPEC: Common Attack Pattern Enumeration and Classification — https://capec.mitre.org
- [15] STRIDE Threat Model — https://en.wikipedia.org/wiki/STRIDE_(security)
- [16] Microsoft SDL, DREAD Model — https://learn.microsoft.com/en-us/previous-versions/ff648644(v=msdn.10)
- https://attack.mitre.org/
- https://en.wikipedia.org/wiki/STRIDE_(security)
- – [17] IPC Systems, Unigy Trading Communications Platform — https://www.ipc.com/products-services/unigy-trading-communications-platform/
- – [18] Cloud9 Technologies Voice Trading Platform — https://www.cloud9tech.com/platform/
- – [19] Speakerbus iTurret Voice Trading Solution — https://www.speakerbus.com/solutions/iturret

