- NAT
- What is ICE and why is it used ?
- Call Flow for STUN protocol exchange
- NAT types
- Network Scenarios for NAT
- Hole Punching
WebRTC : Web-based real-time communications is a gamechanger for real-time communication systems. WebRTC is one such open-source, royalty-free, unencumbered browser-based platform using the browser’s embedded media application programming interface (API). It allows developers to add custom JavaScript & HTML5 to control the media setup and flow. WebRTC has enabled developers to build apps, sites, widgets, plugins and extensions capable of delivering simultaneous audio, video, data, and screen-sharing capability in a peer to peer fashion.
Issues accross Networks : But something which escapes our attention is how media is traversing across the network. Of course, the webrtc sessions run smoothly when both the peers are on the open public internet without any restrictions or firewall blocks. But the real problem begins when one of the peers is behind a Corporate/Enterprise network or using a different Internet service provider with some security restrictions. In such a case the normal ICE capability of WebRTC is not sufficient to set up a bidirectional media streaming setup. For network restriction what is required is a NAT ( Network Address Traversal) mechanism that performs address discovery.
NAT and ICE Solution : STUN and TURN server protocols handle session initiations with handshakes between peers in different network environments. In the case of a firewall blocking a STUN peer-to-peer connection, the system fallback to a TURN server which provides the necessary traversing mechanism through the NAT.

Lets study from the start ie ICE.
NAT
Network Address Translation provides a mapping of internal to external IP addresses. This helps in network address modification for packets which in transit accross a tarfic routinig node such as inter networks.
A private address on the inside of the NAT is mapped to an external public address. Port address translation (PAT) resolves conflicts that arise when multiple hosts happen to use the same source port number to establish different external connections at the same time.
Some ways to acheive this
- Application Layer Gateway (ALG)
- Interactive Connectivity Establishment ( ICE )
- UPnP Internet Gateway Device Protocol
- propertiary SIP based Session Border Controller, so on
Lets us just look at ICE in detail which is the default implementation for WebRTC
What is ICE and why is it used ?
ICE (Interactive Connectivity Establishment ) framework ( mandatory by WebRTC standards ) find network interfaces and ports in Offer / Answer Model to exchange network based information with participating communication clients. ICE makes use of the Session Traversal Utilities for NAT (STUN) protocol and its extension, Traversal Using Relay NAT (TURN)
ICE is defined by RFC 5245 – Interactive Connectivity Establishment (ICE): A Protocol for Network Address Translator (NAT) Traversal for Offer/Answer Protocols.
Sample WebRTC offer holding ICE candidates :
type: offer, sdp: v=0 o=- 3475901263113717000 2 IN IP4 127.0.0.1 s=- t=0 0 a=group:BUNDLE audio video data a=msid-semantic: WMS dZdZMFQRNtY3unof7lTZBInzcRRylLakxtvc m=audio 9 RTP/SAVPF 111 103 104 9 0 8 106 105 13 126 c=IN IP4 0.0.0.0 a=rtcp:9 IN IP4 0.0.0.0 a=ice-ufrag:/v5dQj/qdvKXthQ2 a=ice-pwd:CvSEjVc1z6cMnhjrLlcbIxWK a=ice-options:google-ice a=fingerprint:sha-256 F1:A8:2E:71:4B:4E:FF:08:0F:18:13:1C:86:7B:FE:BA:BD:67:CF:B1:7F:19:87:33:6E:10:5C:17:42:0A:6C:15 a=setup:actpass a=mid:audio a=sendrecv a=rtcp-mux a=rtpmap:111 opus/48000/2 a=fmtp:111 minptime=10 a=rtpmap:103 ISAC/16000 a=rtpmap:104 ISAC/32000 a=rtpmap:9 G722/8000 a=rtpmap:0 PCMU/8000 a=rtpmap:8 PCMA/8000 a=rtpmap:106 CN/32000 a=rtpmap:105 CN/16000 a=rtpmap:13 CN/8000 a=rtpmap:126 telephone-event/8000 a=maxptime:60 m=video 9 RTP/SAVPF 100 116 117 96 c=IN IP4 0.0.0.0 a=rtcp:9 IN IP4 0.0.0.0 a=ice-ufrag:/v5dQj/qdvKXthQ2 a=ice-pwd:CvSEjVc1z6cMnhjrLlcbIxWK a=ice-options:google-ice a=fingerprint:sha-256 F1:A8:2E:71:4B:4E:FF:08:0F:18:13:1C:86:7B:FE:BA:BD:67:CF:B1:7F:19:87:33:6E:10:5C:17:42:0A:6C:15 a=setup:actpass a=mid:video a=sendrecv a=rtcp-mux a=rtpmap:100 VP8/90000 a=rtcp-fb:100 ccm fir a=rtcp-fb:100 nack a=rtcp-fb:100 nack pli a=rtcp-fb:100 goog-remb a=rtpmap:116 red/90000 a=rtpmap:117 ulpfec/90000 a=rtpmap:96 rtx/90000 a=fmtp:96 apt=100 m=application 9 DTLS/SCTP 5000 c=IN IP4 0.0.0.0 a=ice-ufrag:/v5dQj/qdvKXthQ2 a=ice-pwd:CvSEjVc1z6cMnhjrLlcbIxWK a=ice-options:google-ice a=fingerprint:sha-256 F1:A8:2E:71:4B:4E:FF:08:0F:18:13:1C:86:7B:FE:BA:BD:67:CF:B1:7F:19:87:33:6E:10:5C:17:42:0A:6C:15 a=setup:actpass a=mid:data a=sctpmap:5000 webrtc-datachannel 1024
Notice the ICE candidates under video and audio. Now take a look at the SDP answer
type: answer, sdp: v=0 o=- 6931590438150302967 2 IN IP4 127.0.0.1 s=- t=0 0 a=group:BUNDLE audio video data a=msid-semantic: WMS R98sfBPNQwC20y9HsDBt4to1hTFeP6S0UnsX m=audio 1 RTP/SAVPF 111 103 104 0 8 106 105 13 126 c=IN IP4 0.0.0.0 a=rtcp:1 IN IP4 0.0.0.0 a=ice-ufrag:WM/FjMA1ClvNb8xm a=ice-pwd:8yy1+7x0PoHZCSX2aOVZs2Oq a=fingerprint:sha-256 7B:9A:A7:43:EC:17:BD:9B:49:E4:23:92:8E:48:E4:8C:9A:BE:85:D4:1D:D7:8B:0E:60:C2:AE:67:77:1D:62:70 a=setup:active a=mid:audio a=sendrecv a=rtcp-mux a=rtpmap:111 opus/48000/2 a=fmtp:111 minptime=10 a=rtpmap:103 ISAC/16000 a=rtpmap:104 ISAC/32000 a=rtpmap:0 PCMU/8000 a=rtpmap:8 PCMA/8000 a=rtpmap:106 CN/32000 a=rtpmap:105 CN/16000 a=rtpmap:13 CN/8000 a=rtpmap:126 telephone-event/8000 a=maxptime:60 m=video 1 RTP/SAVPF 100 116 117 96 c=IN IP4 0.0.0.0 a=rtcp:1 IN IP4 0.0.0.0 a=ice-ufrag:WM/FjMA1ClvNb8xm a=ice-pwd:8yy1+7x0PoHZCSX2aOVZs2Oq a=fingerprint:sha-256 7B:9A:A7:43:EC:17:BD:9B:49:E4:23:92:8E:48:E4:8C:9A:BE:85:D4:1D:D7:8B:0E:60:C2:AE:67:77:1D:62:70 a=setup:active a=mid:video a=sendrecv a=rtcp-mux a=rtpmap:100 VP8/90000 a=rtcp-fb:100 ccm fir a=rtcp-fb:100 nack a=rtcp-fb:100 nack pli a=rtcp-fb:100 goog-remb a=rtpmap:116 red/90000 a=rtpmap:117 ulpfec/90000 a=rtpmap:96 rtx/90000 a=fmtp:96 apt=100 m=application 1 DTLS/SCTP 5000 c=IN IP4 0.0.0.0 b=AS:30 a=ice-ufrag:WM/FjMA1ClvNb8xm a=ice-pwd:8yy1+7x0PoHZCSX2aOVZs2Oq a=fingerprint:sha-256 7B:9A:A7:43:EC:17:BD:9B:49:E4:23:92:8E:48:E4:8C:9A:BE:85:D4:1D:D7:8B:0E:60:C2:AE:67:77:1D:62:70 a=setup:active a=mid:data a=sctpmap:5000 webrtc-datachannel 1024
| STUN | TURN |
| address discovery for global IP:port | allocates its own address as interface to the client |
| binary protocol | extension of STUN |
| doesnt stay in path after connection | stays in path after connection. tunnels and relays media |
| higher priority | lower priority |
| server and peer reflexive ICE candidates | relay ICE candidates |



Call Flow for STUN protocol exchange
Client -> Server : binding request with attributes – CHANGE-REQUEST
Server -> Cient : binding response with attributes – MAPPED-ADDRESS, RESPONSE-ORIGIN, OTHER-ADDRESS, XOR-MAPPED-ADDRESS



WebRTC needs SDP Offer to be sent to B from A.
Client B uses this SDP offer to generate an SDP Answer for A.
The SDP ( as seen on chrome://webrtc-internals/ ) includes ICE candidates which map open ports in the firewalls.
However, in case both sides are symmetric NATs, the media flow gets blocked. For such a case TURN is used which tries to give a public IP and port mapped to internal IP and port. This relay path provides an alternative routing mechanism like a packet mirror. It can open a DTLS connection and use it to key the SRTP-DTLS media streams.
NAT types
Some types of NAT are described below
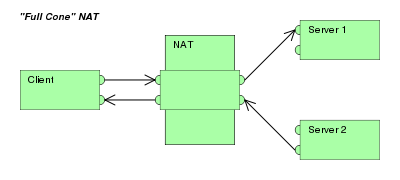
Full Cone ( Normal)
All requests from the same internal IP address and port are mapped to the same external IP address and port. It also allows external hosts to send packet to internal host by using the mapped external address.
Restricted Cone
All requests from the same internal IP address and port are mapped to the same external IP address and port, but external hosts can send packet to internal host only if internal host had previously sent a packet to that IP address.

Port Restricted Cone
All requests from the same internal IP address and port are mapped to the same external IP address and port, but external hosts can send packet to internal host only if internal host had previously sent a packet to that IP address and that port.

Symmetric
All requests from the same internal IP address and port, to a specific destination IP address and port, are mapped to the same external IP address and port. Any traffic from same internal IP+port to a different destination uses a new mapping. Also external hosts which receives a packet can send a UDP packet back to internal host.

Address and Port-Dependent Mapping (“APDM”) and APDF (Address and Port-Dependent Filtering).

credit https://web.archive.org/web/20180829131023/http://nattest.net.in.tum.de/results.php
Network Scenarios for NAT
In order to Understand this better consider various scenarios that determine the NAT Mapping Behavior one could run tests using cli or network analyzer tools and checking checking the XOR-MAPPED-ADDRESS value of the Binding Response message that the client receives
Mapping behaviour
- Endpoint-Independent Mapping NAT (EIM-NAT)
- Address-Dependent Mapping NAT (ADM-NAT)
- Address and Port-Dependent Mapping NAT (APDM-NAT)
Filtering behaviour
- Endpoint-Independent Filtering NAT (EIF-NAT)
- Address-Dependent Filtering NAT (ADF-NAT)
- Address and Port-Dependent Filtering NAT (APDF-NAT)
Hole Punching
As long as one end of the connection is able to determine the dynamic association of thee other [arty by NAT and send data , hole punching can work.
Permissive NAT mapping techniques which map the same internal address/port consistently to an external address/port are suitable for hole punching such as full cone , address or port restricted NAT. However pure symmetric NAT have inconsistent destination specific port mapping and thus cannot do hole punching.
1 . No Firewall present on either peer. Both connected to open public internet
Diagrammatic representation of this shown as follows :

In this case there is no restriction to signal or media flow and the call takes places smoothly in p2p fashion.
2. Either one or both the peer ( could be many in case of multi conf call ) are present behind a firewall or restrictive connection or router configured for intranet
In such a case the signal may pass with the use of default ICE candidates or simple ppensource google Stun server such as
iceServers:[
{ 'url': "stun:stun.l.google.com:19302"}]
Diagram :

However the media is restricted resulting in a black / empty / no video situation for both peers . To combat such situation a relay mechanism such as TURN is required which essentially maps public ip to private ips thus creating a alternative route for media and data to flow through .

Peer config should look like :
var configuration = {
iceServers: [
{ "url':"stun::"},
{ "url":"turn::"}
]};
var pc = new RTCPeerConnection(configuration);
3. When the TURN server is also behind a firewall
The config file of the turn server need to be altered to map the public and private IP. The diagrammatic description of this is as follows :

References :
- RFC 3489 STUN – Simple Traversal of User Datagram Protocol (UDP)Through Network Address Translators (NATs)
- RFC 5928 Traversal Using Relays around NAT (TURN) Resolution Mechanism
- webrtchacks https://webrtchacks.com/symmetric-nat/
- netmanias https://www.netmanias.com/en/post/techdocs/6067/nat-network-protocol/nat-behavior-discovery-using-stun-rfc-5780
- wikipedia https://en.wikipedia.org/wiki/Network_address_translation

Have read several of your WebRTC-related postings. All of them correct and informative at an introductory level. But because of that level, they are also very close to being entirely redundant, given other sources available on the web. They also seem to be largely cut-n-pasted from such sources and pieced together with marginal grammar and typography. How much of this may be due to English-as-second-language is not clear. Your time and effort may be better spent on original contributions about less well-covered topics.